The above terms might look like the name of an up and coming indie band with an elaborate name, but actually all 3 terms are one in name, but just vary in terms of their output.
MD5 (Message Digest algorithm 5), SHA1 (Secure Hash Algorithm 1), and SHA256 (Secure Hash Algorithm 256) are all very different sounding names, but actually, all work come under the same umbrella of Cryptographic Hash Functions. These are used in digital security to better help protect your system and ensure you have downloaded the uncorrupted, original files as intended by the sender.
It additionally is used by software companies in protecting your information, many high level passwords are coded in SHA512. Much like binary code and hexdecimal, these bits and pieces of numbers / letters can also form a series of words and letters but can also be used to verify the integrity / authenticity of a file. It is popularly used for verifying huge software file downloads like those of Ubuntu, Photoshop, etc.
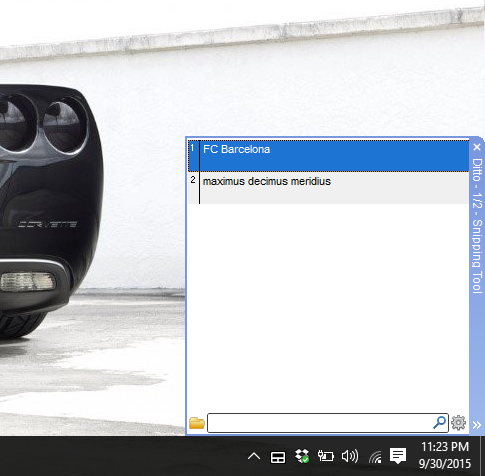
When we come to the former part of the above sentence, it is best I show you a first hand example of what is being told.

As you can see in the above image, especially where highlighted, these are MD5 hash values. As mentioned prior, MD5, like its siblings, can also be used to turn letters / numbers into what we call hash values (9d5502b6b6bf9743baedd9b0040e92d1 is an example of a MD5 hash value), and the output we have is Yash2134.
This not only applies to MD5, but also to SHA1 / SHA256 checksums too. While SHA1 is considered to be outdated, SHA512 has more uses by major companies in protecting their data, but of course isn’t available for commercial use due to obvious reasons.
While some of you might be thinking “MD5, SHA1, and SHA256 look really useful for keeping passwords. I could just use the word potato, run it through a SHA256 and use the SHA256 hash as a password!”
Doing so would be HIGHLY ill-advised since anyone who knows how to differentiate this code will need the span of an hour or maybe even less to figure out you are using MD5 / SHA data and reverse engineer your password if you happen to leave the hash on your clipboard.
For now, this is as much as I would like to get into when talking about the basics of these 3. The main purpose of this article is to help educate and inform YOU, the reader, about the added benefits of using File Hasher [Windows Store] and the benefits it will give you regarding verifying your apps, or other media on the system.

Using File Hasher is as simple as just clicking on Open File and navigating to the file you wish to put under the microscope. The only rule is the file you run HAS to have an extension (exe, MP3, MP4, Avi, jpg, png, etc.), You can’t run the checksum on folders or otherwise items which have no extension.

While you might not be able to make uber 1337 passwords with the above, you can use them for a different purpose, to verify that you have the same version of a program, video, MP3, etc as it is supposed to.
With the help of File Hasher, you can now cross check your file and make sure you have the real McCoy instead of a forgery or otherwise outdated version of your software.
We can see the examples of Winmd5, a similar software, below:


You can see in the 2 images that the highlighted portions are the same with the MD5 checksum / Hash that is showing in the application, thus verifying that we have the authentic, original file.
Another use of this app can potentially be if you and a friend play the same game, you can both run the games .exe file in the software and exchange any of the 3 Hash functions to determine if one of you is running an outdated game.
You can see below my hearthstone.exe and right below it the hearthstone.exe of a friend, we both are on the latest version of the game and as you can see, we have matching versions in all the boxes.

Now let’s see another aspect of this software. When the same friend and I compare Google Chrome you will see a clear difference. You might be asking “But you just said two software’s will ALWAYS have the same hash / checksum, so why are your versions of Chrome different?”
This is where we see a difference, the reason why my friend and I have a disagreement on the Google Chrome results of our hash functions is because we are on completely different versions of the same software.

Where I am using Chrome 51.0.2704.36 beta-m (64-bit) My friend is using the 32-bit variant of Google Chrome.
We hope that now you understand the benefits and otherwise uses of the 3 hash functions. If you ever come across instances where the software comes with attached MD5 / SHA1 / SHA256 checksums, you can put said file in this and verify the integrity is intact, the way we demonstrated with Hearthstone.exe and winmd5.
If you have any further questions, let us know in the comments section below!
The post Check MD5, SHA1 & SHA256 Hash With File Hasher For Windows 10 appeared first on Windows Clan.